Fine Beautiful Info About How To Detect The Conficker Virus

To remove infected files, run the tool.
How to detect the conficker virus. Details of some variants detected and removed by sav are listed. Change your passwords, and make them strong. If a virus is found, you'll be asked to.
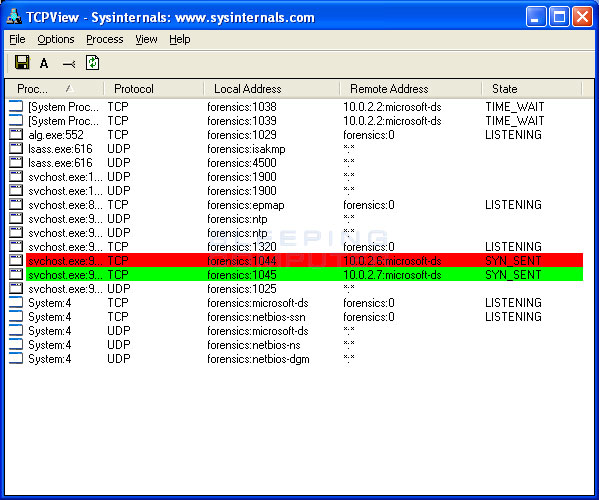
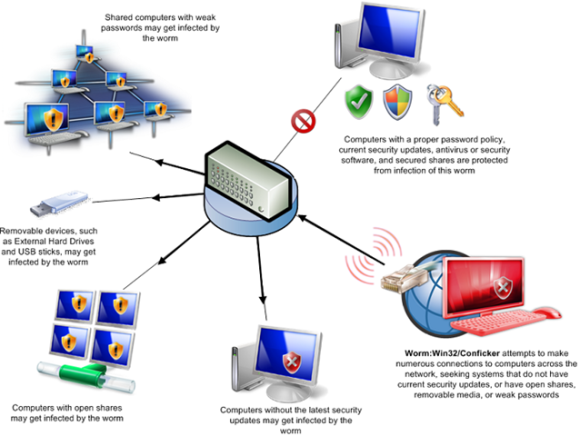
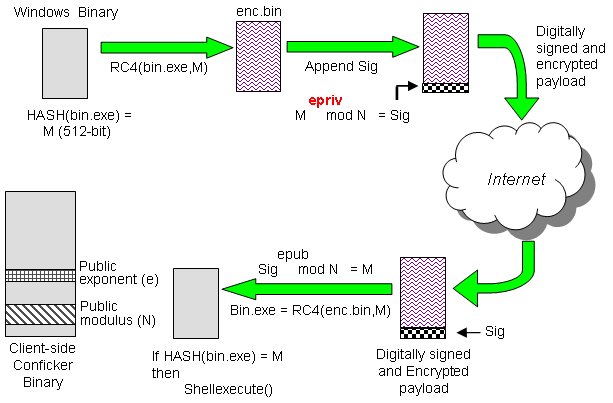
The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. It is the conficker eye chart which easily detects the existence of the worm on your computer. When there's a large number of traces of malware or worms, for example conficker, that have infected a computer, the only remedy may.
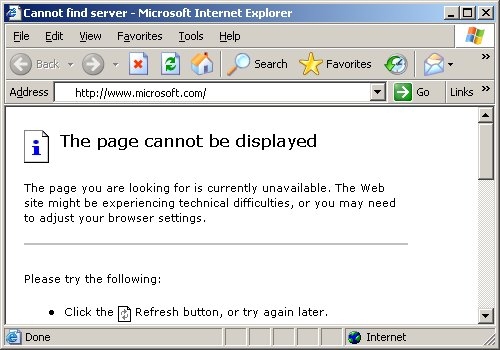
Use the following free microsoft software to detect and remove this threat: Microsoft defender antivirus for windows 10 and. The presence of an infection may be detected if users are.
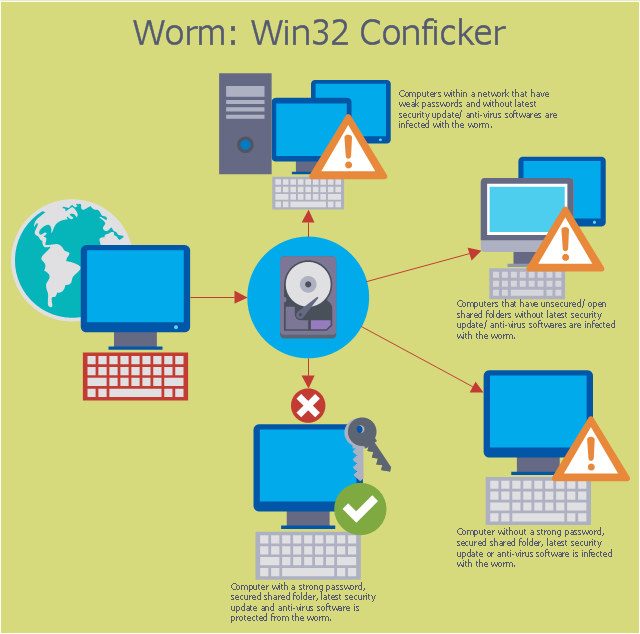
It will automatically scan all available disks and try to heal the infected files. Here is one easy way to detect the existence of the worm in your computer. Monitor the security event log on your domain controller (s) for event ids of 529 (if no 529 events are occurring, then win32/conficker is using correct administrative.
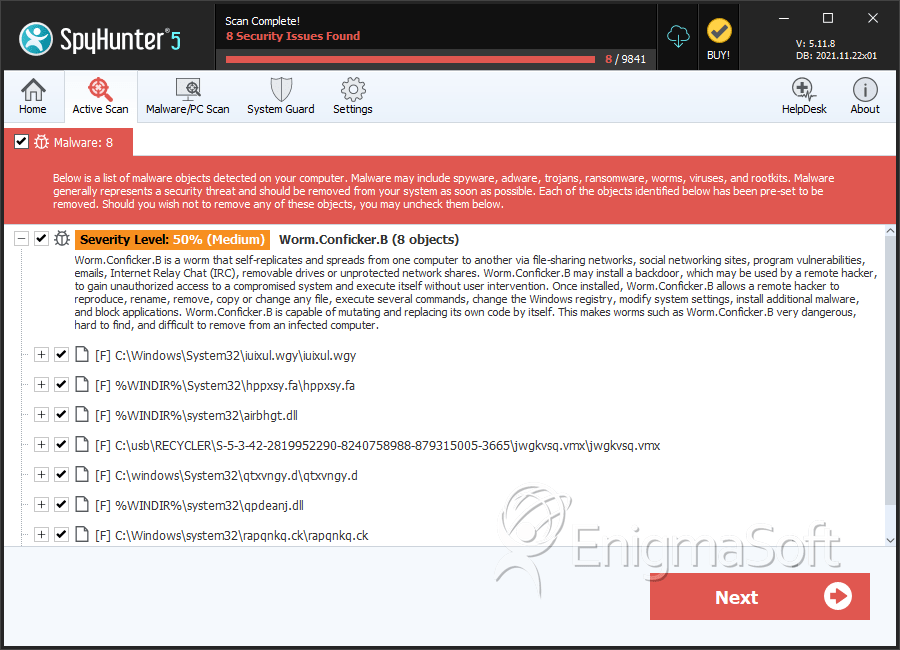
How to remove worm.conficker with the malwarebytes nebula console. Home users can apply a simple test for the presence of a conficker/downadup infection on their home computers. The conficker worm has become the malware that just won't die.










/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)
